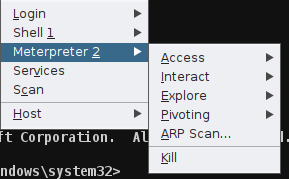
Armitage#
Armitage is a GUI interface for the Metasploit Framework, built by the same team. It’s great for collaboration between teams too.
Install#
git clone kalilinux/packages/armitage.git && cd armitage
bash package.sh
Files should now be in ./release/unix/
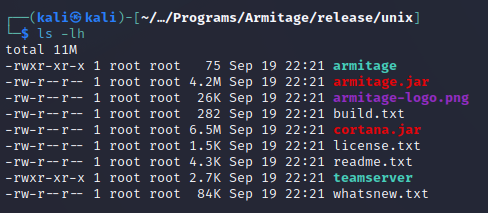
The fun files here are:
TeamServer: Creates a server for the team to use. It must be passed
IP address
Shared Password
Armitage: Used to connect to a server. It gives you a screen to log in with. The username is a ‘nickname’
this is actually in the kali repos now, can just install armitage
same with teamserver
Prepare The Environment#
Since it uses metasploit, make sure its all worky
Start the DB
sudo systemctl start postgresql
Clear the DB
sudo msfdb delete
ReInitialise
sudo msfdb init
Start & connect#
Make sure youre in the right directory:
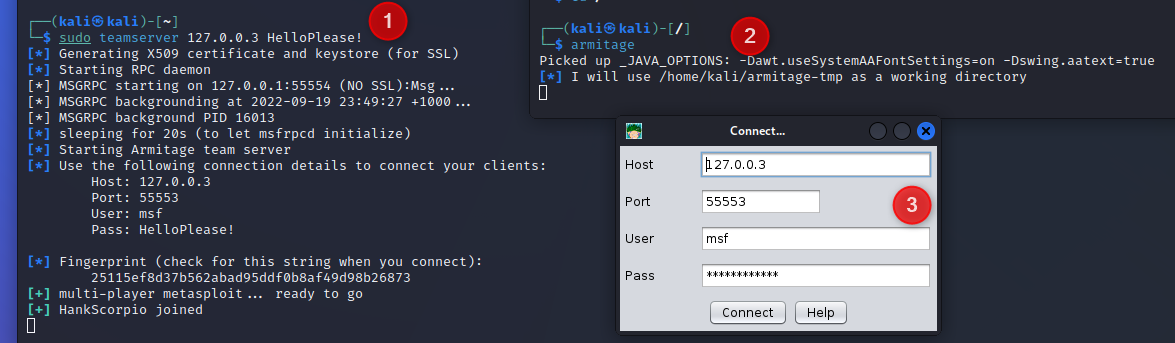
sudo teamserver [ip] [password]
Open a new terminal
armitage
teamserver gives the logins, use msf as your user and the above password
Make It Do Fun Things#
Start a Scan#
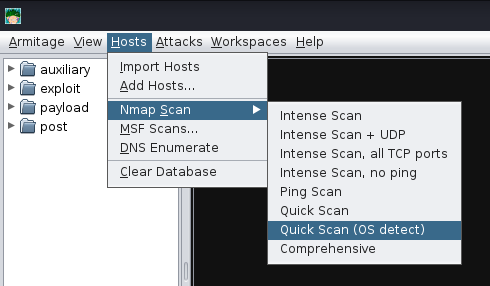
You’ll get a window for a target, can do an IP or a subnet. Quick or OS detection doesnt give the -vv option though….
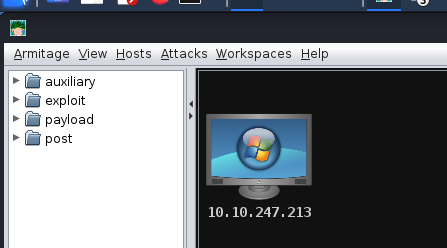
I did “10.10.247.213”
After a while, the scan completes and I get a new host on my display
Run Exploits#
You can now open exploits and pick your attack. Drag drop the attack to the host and you can now set your arguments and let it run
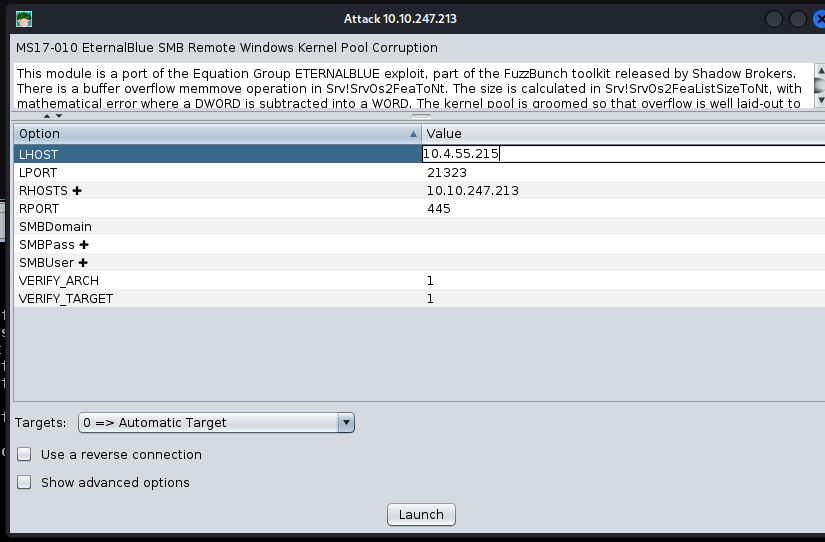
If it works, it gets all Thor-d
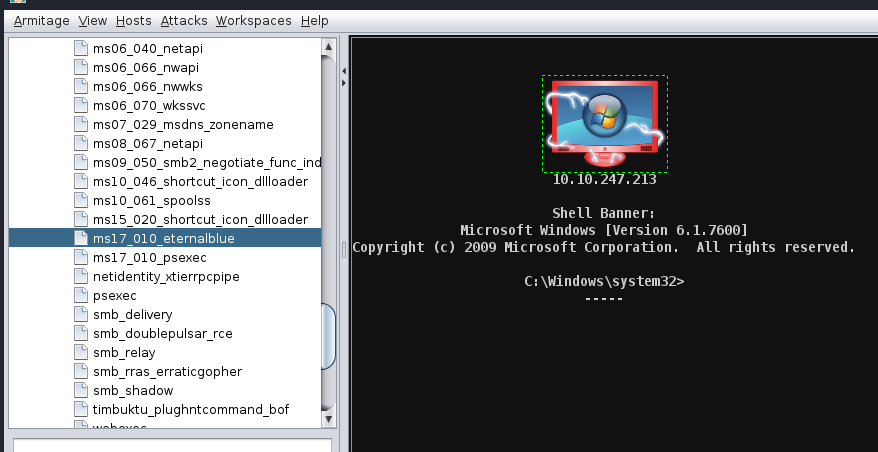
Run POST modules#
You can then right click and take control of the shell
Most of the time, you will want to excalate this to a meterpreter shell. Right click the host and select your shell, then Post. It will expand your tree to show the post modules. Under manager is the shell_to_meterpreter module. Run it and will attempt to create a second shell for meterpreter.