OpenVAS#
THM Room : https://tryhackme.com/room/openvas
Web App and endpoint scanner for vulnerabilities. Part of GreenBone Vulnerability Management solution.
Taken from : https://tryhackme.com/room/openvasTaken
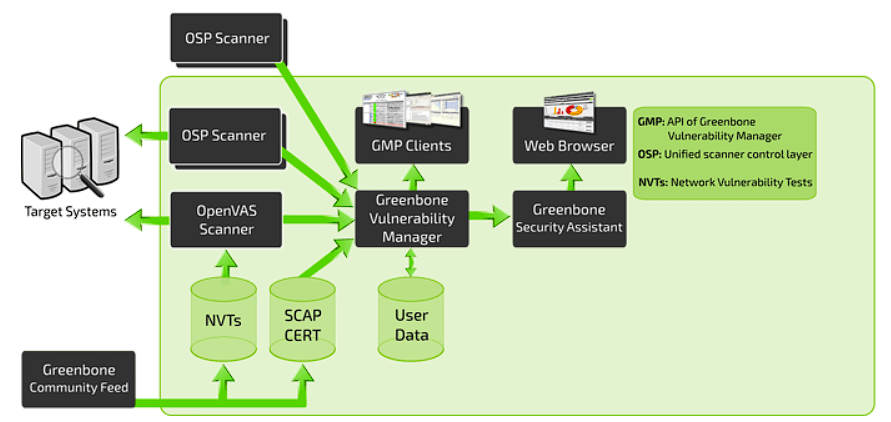
The current state of OpenVAS is it being integrated to the greenbone secuirty suite. You cant get an installer just for OpenVAS now, you need the whole package. As below, you can get it as an appliance though, which is quite useful. The difference between the ‘free’ and enterprise versions is the streams made available to you. The enterprise one has the full up-to-date stream (with the newest models), while the free one uses a community feed.
Installation#
From Repos: https://websiteforstudents.com/how-to-install-and-configure-openvas-on-ubuntu-18-04-16-04/ https://www.agix.com.au/installing-openvas-on-kali-in-2020/
From Source: greenbone/openvas-scanner
For Docker (prefered) mikesplain/openvas-docker https://hub.docker.com/r/mikesplain/openvas/dockerfile
apt install docker.io
docker run -d -p 443:443 –name openvas mikesplain/openvas
Updated since I ran the THM room, there is also now a VM appliance available. This is how I set mine up in my lab. You can’t find the ‘free’ one any more, it’s not that it doesn’t exist, you just have to get the enterprise trial and it stays free.
Can then open in 127.0.0.1 (browser over port 9392)
Default credentails admin/admin
First Steps#
Assuming you have run the initial setup and logged in….
Make a target#
Like most (all?) vulnerability scanners, you need to start by creating targets to scan. First open the “Targets” page then select the “new targets” button.
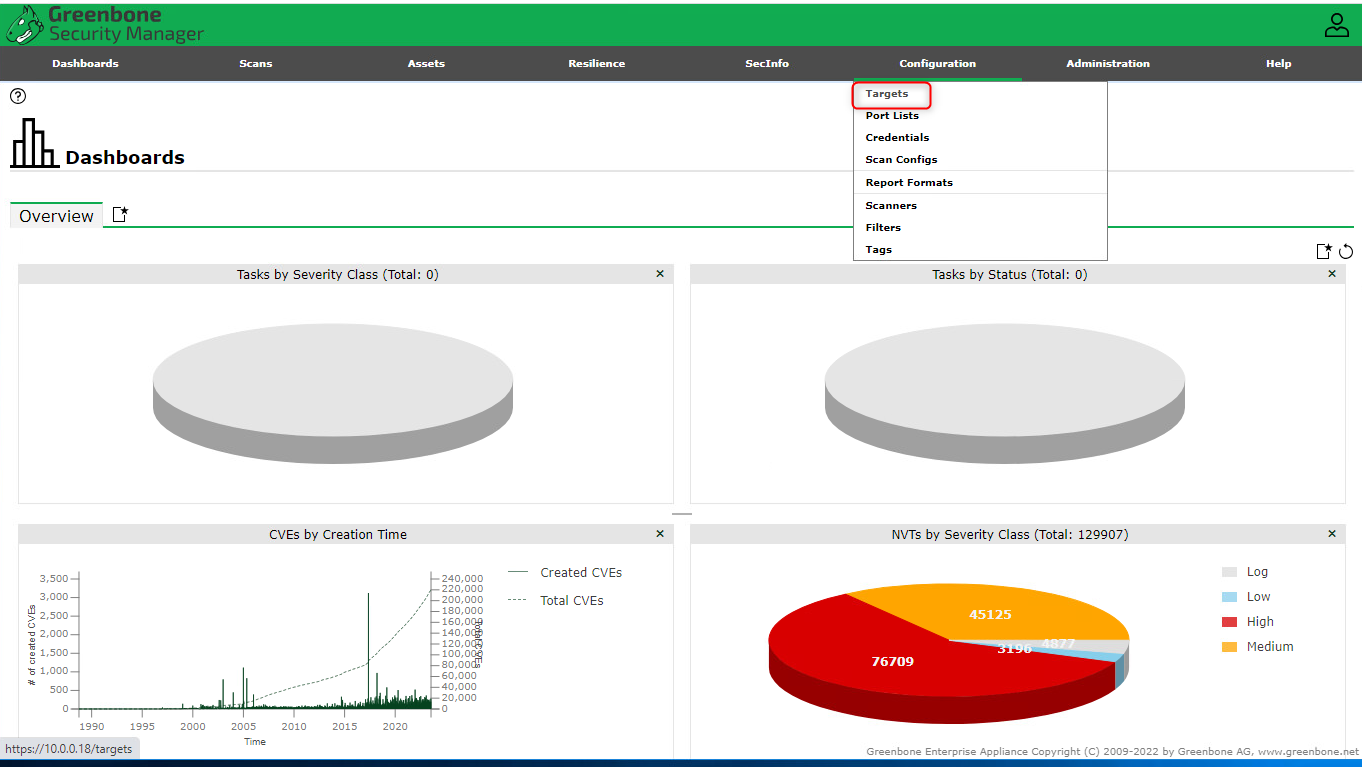
In this instance, we are adding the entire local subnet (I’m only using the first /24 subnet in my lab)

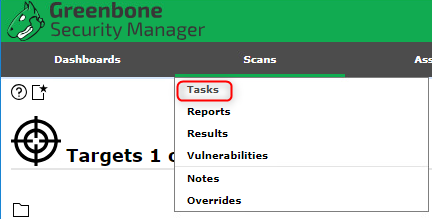
Add a task#
Now that we have a defined group of targets to interogate, we need to create a task. A task is basically an action to run against a target (or group of targets).

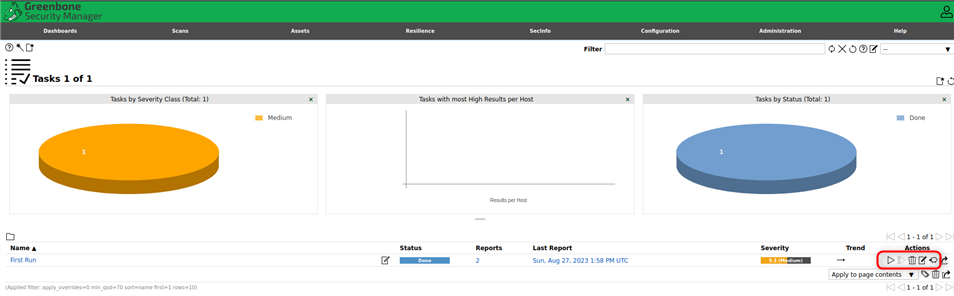
Run the task#
Now we can do the things.