Yara#
Yet Another Ridiculous Acronym…. I think I’m going to like this software :-)
The Basics#
What Is Yara?#
Yara is a defensive software that can be used to analyse ‘data’ to assist with detection of possible threats. In this case, data refers to ‘files’. This is achieved via pattern matching.
Installation#
Standard for linux:
sudo apt install yara
For everyone else, visit the repo on Github: virustotal/yara
How Does it Work?#
Yara is a system to create rules in the file system. It can also run these rules against a defined directory. In general, you create a group of rules and then use these to ‘audit’ a destination as required. There are many rules available publicly, we’ll get to this a bit shortly.
The rules themselves are quite simple, however the strength of Yara is how these rules are applied by the technical team. A rule itself is a file, and must also include a ‘destination. This can be a path, directory or ProcessID. The format is:
yara [rule].yar [destination]
A .yar file is a rule file. When the rule is ‘met’, it reports with the name of the rule defined in the file. An example rule, shown below, is taken from [https://tryhackme.com/room/yara](TryHackMe’s Yara Room)
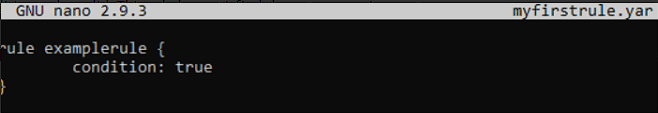
Rules#
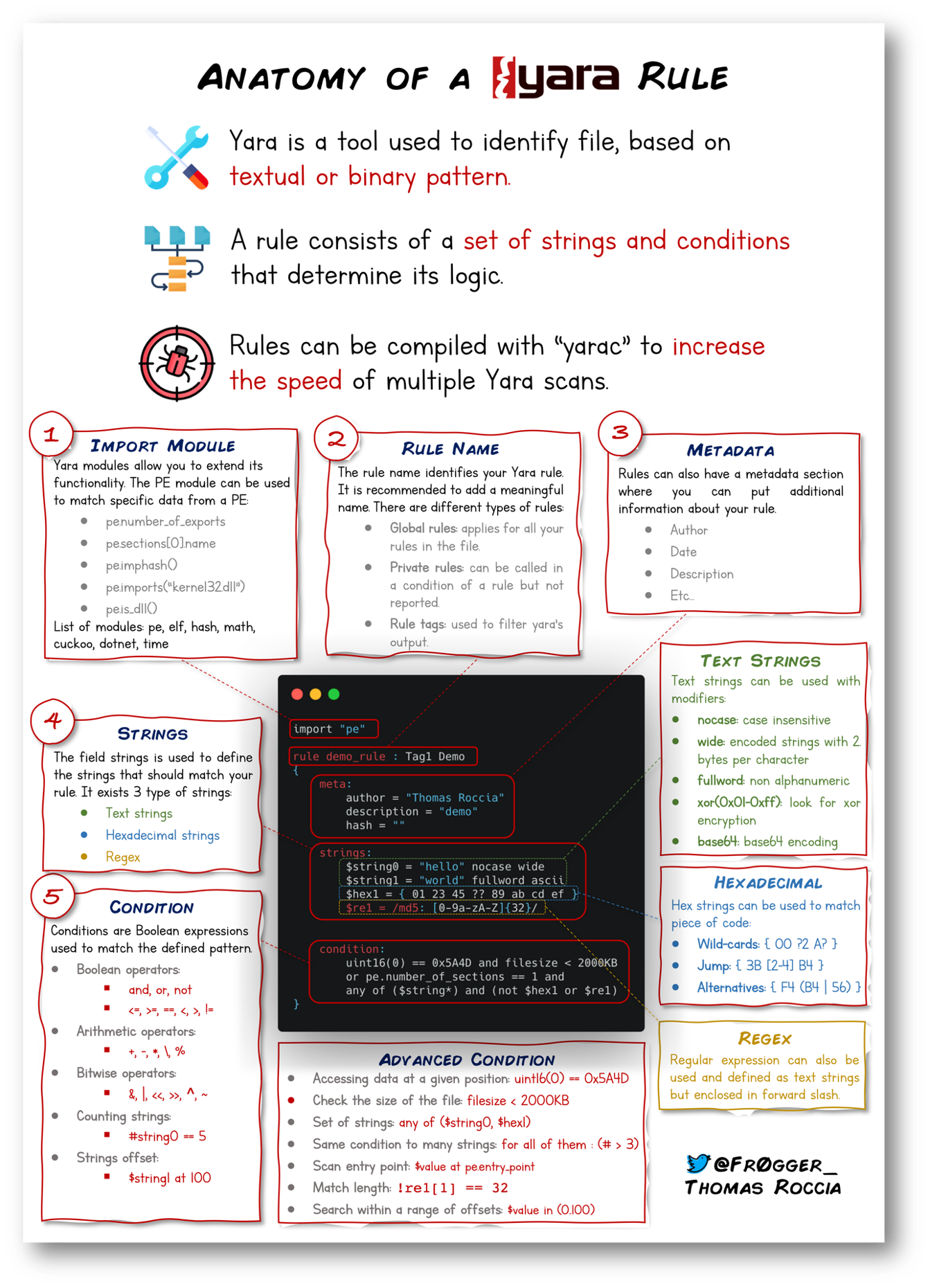
The rule file can be populated with many different kinds of ‘checks’, he full list of rules can be found here
On the rules note, there also a great infograph available: https://blog.securitybreak.io/security-infographics-9c4d3bd891ef#18dd
The Expansion Packs#
So, we’ve covered the basics about Yara, but Yara also has a lot of friends that really help it shine. Oddly enough, these are all by the same person. Thanks :-). Each of these could be their own page, but I dont know enough about them… yet…
LOKI#
Loki is an analysis software that can be used to create yara rules to identify a suspicious file using the yara’s rules. It can assist with IoC (Indicators of Compromise). Loki itself is a python file which must be set up with directories before it can be used. To run Loki against a file
Enter the same directory
Run the remote script against the current directory
(ofcourse you can reverse this and call the directory from the python script location… or both)
python ../tools/Loki/loki.py -p .
If nothing is found, you’ll get a ‘no issues found’
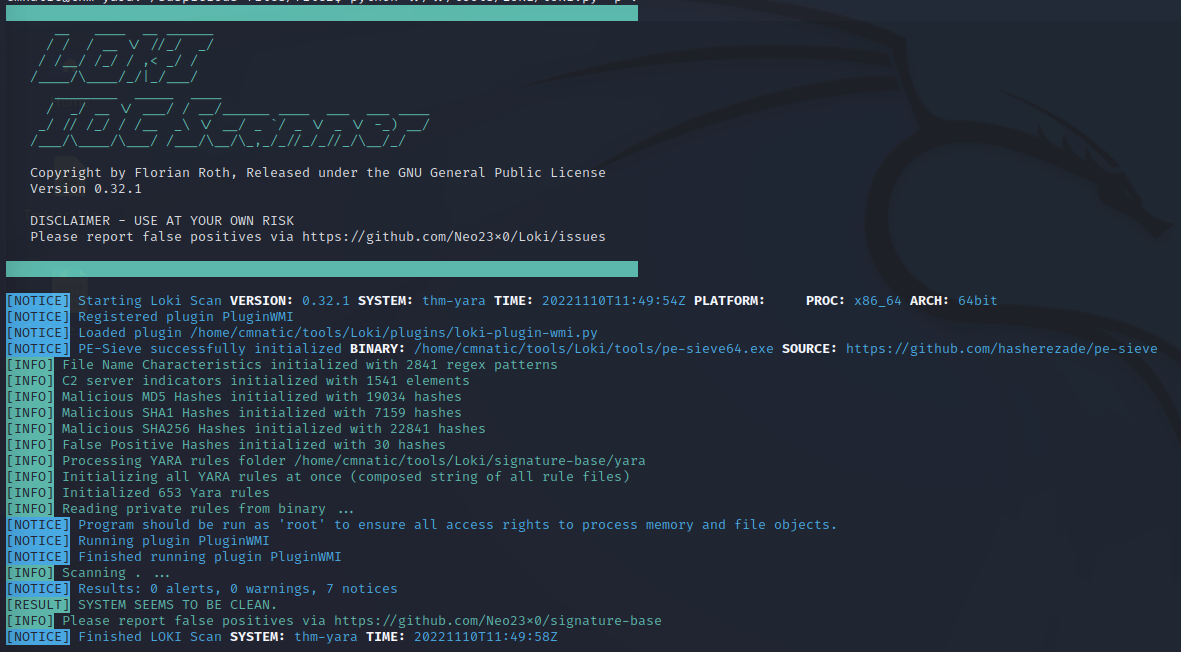
But more importantly, if something is found, it will report the yara rule and information about what was found
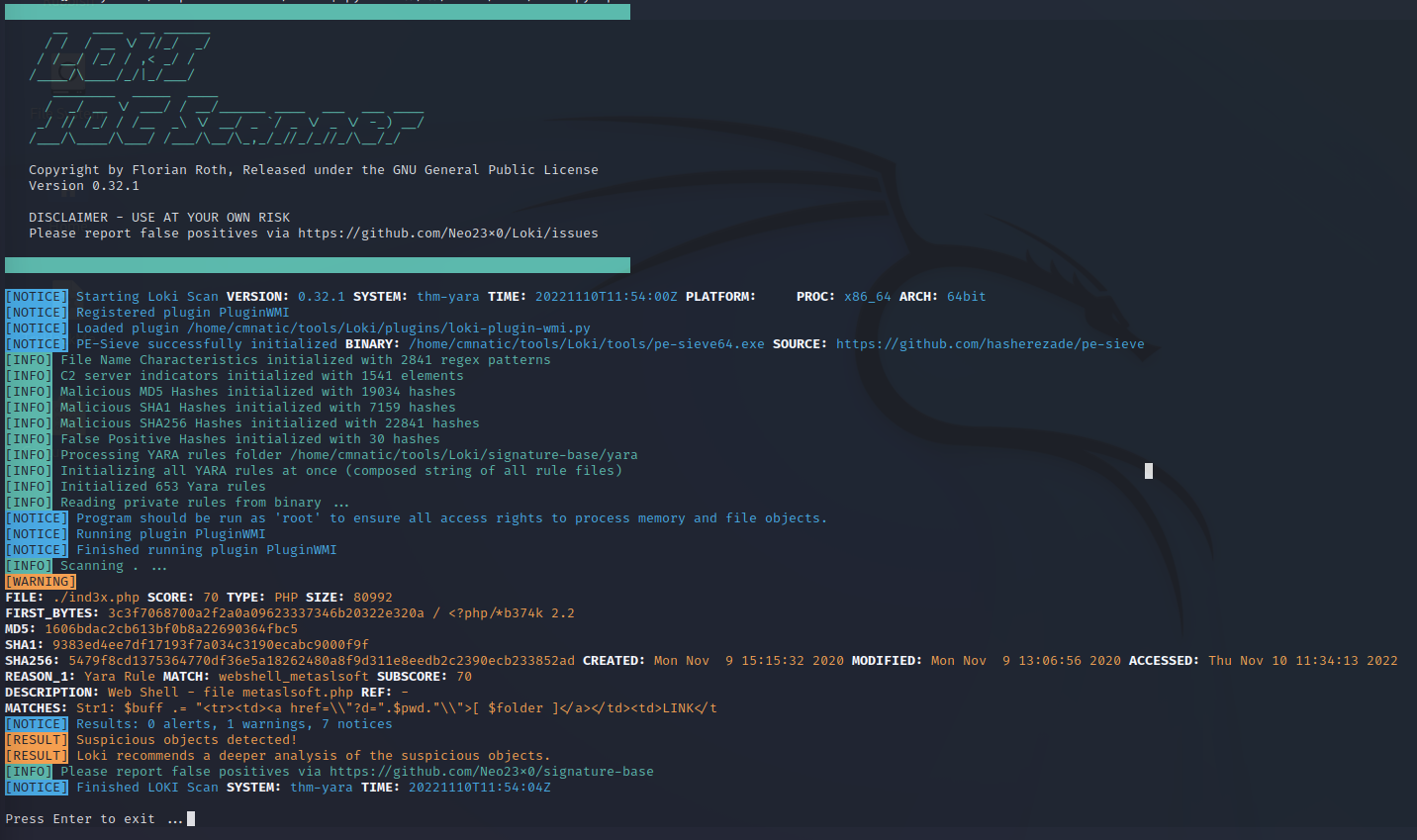
The key word here is ‘if nothing is found’. The scan is only as good as your rules. In these screenshots, they are both actually infected.
THOR#
FENRIR#
YAYA#
YarGen#
As you should have been able to work out from the above, these tools are only as good as the rules which yara has. So how do we improve this? The obvious answer is to update your rules, but you can also add a known suspicious file and have YarGen create these rules for you. YarGen stores a DB of well known ‘good’ strings, and excludes these when creating your new rule. Nice. Make sure you update your YarGen before creating the rule.
python3 yarGen.py -m [suspiciousfile directory] –excludegood -o [where to output the .yar file]
If youre then adding this to Loki, it goes in the Loki/signature-rules/yara folder
