The Basics#
So, you’ve decided to start your path in Cyber Security, or more likely, hacking sounds fun. Great! It can be! But there is more to it than getting a hoodie and balaclava and hunching over a laptop (in the dark obviously). Hacking is a career path, regardless of what popular media tells you about hackers.

What is Cyber Security?#
The CIA Triad#
The CIA triad is one of the fundamental concepts of Cyber Security and encompases the domains that need to be protected. As a side note, it doesnt mention human protection, but this should be considered the priority in all domains.
CIA doesnt refer the the US Government agency, but rather Confidentiality, Integrity and Availability. Without all 3 domains protected, you are in a vulnerable state.
Confidentiality#
This domain is focused on protecting access to information and ensuring only authorised users/devices can access protected data. This could include access control, encryption & IAM.
Integrity#
Integrity is ensuring that data hasnt been modified, and if it has you know who did. This includes checksums, Non-repudiation and backups.
Availiablity#
Lastly, Availibility is making sure that services & data can be accessed and aren’t ‘offline’. If someone is authorised, they should be able to access information.
Terminolgy Used#
There is a large amount of jargon used when discussing attacks. The below shows how this looks in an overarching scale
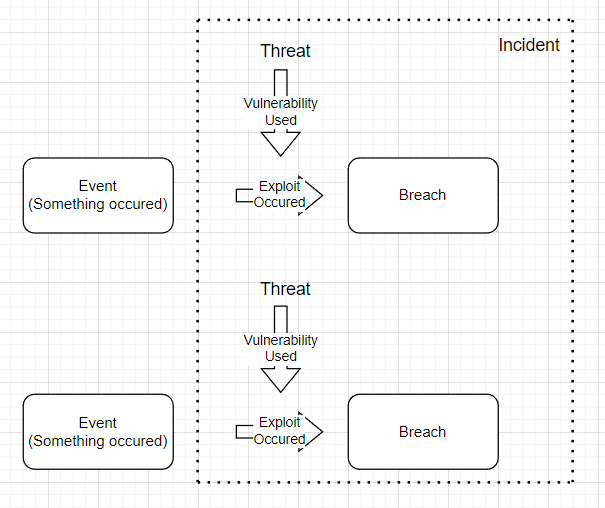
A THREAT is any person/group/organistion who isn’t following the ‘green path’ so is therefore attacking the system
An EVENT is any recordable action performed by a THREAT. This could be a ports scan, attempted SQL injection or a failed password attempt
A VULNERABILITY is any weakness in the system
A THREAT can EXPLOIT a VULNERABILITY to access the system outside their expected access. This is a BREACH
An INCIDENT can be one or many linked BREACHES or EVENTS
