Nessus#
Nessus is an automated vulnerability scanner for Web Applications and on-prem devices. It includes quite a few modules, and MANY pluggins to make it rather easy to scan a web application in search of Bug Bounties vulnerabilities. There is a free edition but it requires registration for an activation key. I’ve only done a bit on this so far but it looks like a great tool to add to the Active Scanning stage of an attack. You can start here.
You may be wondering why this is in Blue Team if it’s helpful for Active Scanning? Well, if you’re on the blue team, you should be considering running vulnerability scans against your own infrastructure on the regular.
Installation#
For my lab, I have installed Nessus as an Appliance. Your steps may differ if you add to a Windows or Linux box.
Download the “Tenable Core Nessus” Appliance
Import the OVF
Launch the OVF, set IP settings & create a web application User
Connect to the web portal (Based on the IP you set earlier). You’ll need to enter your registration settings.


It will then sit downloading plugins etc. Once done you’re good to proceed.
Launching#
Once you have Nessus installed, it must be started on your device as a service. This isnt needed if running the appliance.
sudo /bin/systemctl start nessusd.service
You can then open it on the local machine on port 8834 (in a web browser)
http://[IP]:8834
And log in

Scanning#
Most of the time, you are either wanting to scan or see the report for another scan. To create a basic scan
Select the “Scans” tab at the top
Create a new “Scan” on the top right
Start with a basic scan, use your whole subnet (assuming its not massive and youre allowed to…)
~~Fire ze missiles~~ Kick off the scan.
Go make a coffee
Come back and see your report… or a dead site… Either way; if you havent done this before it probably wont look pretty.
Here’s my Lab
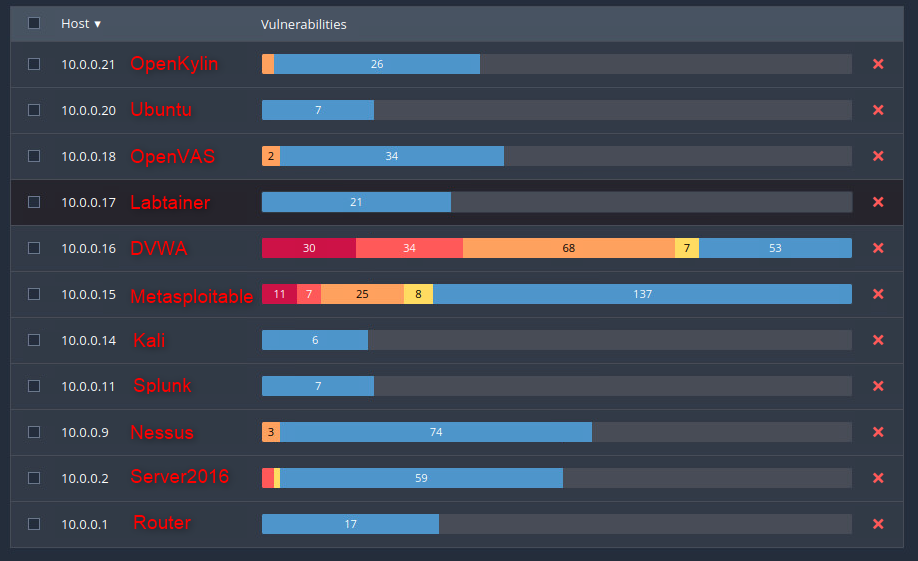
Theres a few insights I’d like to share from here.
DVWA and Metasploitable have a LOT of vulnerabilities. Theres no suprises here.
Server2016 has no critical issues found, thats actually surprising (though at time of writing, Server2016 still has extended support)
Nessus & OpenVAS are both appliances but still have some medium level vulnerabilities found
Splunk, Kali & Ubuntu are all fully patched ubuntu boxes, so expected their results to be about the same
OpenKylin is also one though, interesting that it has SO much more in the info. Same with Labtainers
Now, of course you can only take these results as an indication at best. A lot of the mediums are SMB signing which may not even be used by the environment. At best, what we’ve done so far is purely script kiddie level. The skill from here comes in understanding what is relevant (and can be exploited) and what can be ignored.
